DDoS Attack and Web Application Firewall
February 8, 2019
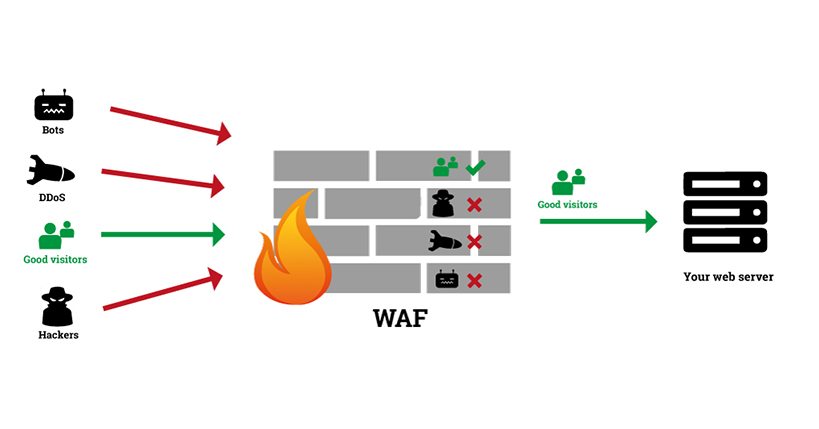
What is DDoS Attack and Web Application Firewall?
Distributed Denial of Service (DDoS) attack is a type of DoS (Denial of Service) attack. Multiple systems flood a network or server with fake requests to disrupt the targeted website’s normal operation. Generally, DDoS attack online originates from several compromised computers. As fake requests are coming from different IP Addresses, you need an effective DDoS attack prevention tool to keep your business online.
We have used a Web Application Firewall (WAF) to protect several websites of our clients. The most popular web application firewalls are Incapsula and Cloudflare. These services sanitize traffic to a website by blocking DDoS requests. Legitimate requests are forwarded to your website. This way, your website stays online to serve your users.
Recently we came across a need to decide on which cloud-based WAF (Web Application Firewall) to use for one of our clients. We needed DDoS protection at the network and application layer. We considered both Incapsula and Cloudflare. We are going to talk about the configuration of both services here. We have used both services and also switched from one to the other. The understanding configuration is vital before we start using any of these services.
Incapsula
DNS Changes
Incapsula provides a couple of static IP addresses where you can point to your domain’s A records. This means you don’t need to change the NS records of your environment. Traffic will go to your hosting provider and then it will be routed to Incapsula. Incapsula will check and sanitize traffic as required and then send it back to your server.
You need to provide the IP of your server as “Origin Server” in Incapsula. In my case we were using a load balancer (AWS ELB), so we entered the DNS of the load balancer as the origin server.
If you are looking at protecting your HTTP traffic, you don’t need to change your domain’s other DNS entries. This way starting with Incapsula is very easy.
Reverse Proxy
By default, return traffic from the website to the client browser is sent directly. You can request Incapsula to work as Reverse Proxy also. So that return traffic is also routed via Incapsula. Reverse Proxy hides your server IP from the public and attacker. We have recently seen that sometimes attackers target your website using the origin IP addresses of your server or load balancer to bypass WAF. The reverse proxy is a good option to prevent this type of attack.
They are turning off Incapsula temporarily.
You can go to the Websites page in Incapsula and select the “Disable” option from the More menu. If you are using Incapsula provided SSL Certificate, you must have an SSL Certificate installed on your server. Otherwise, your customers will start seeing SSL Certificate errors in their browsers.
RTE Editors
Relatively small issue, but if you have RTE editors on your website’s administration panel, Incapsula can block post requests as they contain HTML tags. You can whitelist your IP address in Incapsula to prevent this. If you are on dynamic IP, this can be a bit annoying.
Cloudflare
DNS Changes
We needed to change NS entries of the domain to route traffic via Cloudflare. We changed them from the domain hosting provider. We also needed to transfer ALL our DNS entries like A records, MX entry, and other CNAME or TEXT entries we had for domain validation, SMTP, VoIP, and VPN services. The good thing is when we added a domain to Cloudflare, it automatically detected and added most of the DNS entries automatically. We had to enter the remaining few entries manually.
As we can’t have ELB DNS as A record, we added CNAME records for the root domain and “www” subdomain pointing to ELB DNS.
Reverse Proxy
Cloudflare by default acts as a reverse proxy to a domain. So response form from the webserver goes to Cloudflare first, and then it is passed back to client browsers. This way, your server IPs are not exposed to the public or attackers.
They are turning off Cloudflare temporarily.
We had a live streaming event on the website, so we wanted to check if we can bypass Cloudflare if required. We didn’t want a lot of our customers to see captcha challenges. The two possible options found.
Security level – By default security level is set at “Medium.” we have the option of reducing it to “Essentially Off”.
Pausing Cloudflare – There is an option to pause Cloudflare to send traffic directly to web servers. It takes few minutes before traffic starts going now to your servers. It turns off all Cloudflare services including SSL. If you are using Cloudflare provided SSL Certificate, you must have an SSL Certificate installed on your server. Otherwise, your customers will start seeing SSL Certificate errors in their browsers.
RTE Editors
Cloudflare sends a Captcha challenge when you submit a form containing an RTE editor (HTML tags). Once you pass the captcha, your form will be submitted successfully.




